Web app testing and Cloudflare

Intro
In this article we will perform some basic tests to validate our Cloudflare security settings and explore the logging features of Cloudflare's security analytics. We will use tools like Kali linux to perform these tests. Please note that while we will use some web application security testing tools, this article is not an in-depth tutorial on such tools. We mainly aim to perform some basic validation of our Cloudflare security.
Disclaimer: Running security testing tools should only be done on sites where you have explicit permissions to perform such tests. Running security tests, a.k.a., penetration tests on sites you don't own or don't have permissions to scan can be a violation of the law
Now back to the show...
In the toolbox
- Kali Linux
- WhatWeb
- WPscan
- Nikto
- Wapiti
Web security overview
Anyone that has run a website exposed to the Internet that has ever checked their webserver logs knows that it will be scanned, probed, and attacked by all sorts of bots, script kiddies, and hackers. The open Internet is the wild west and traffic of all sorts (legitimate and malicious) will be sent to your site. Most of these probes and scans are looking for low hanging fruit; web servers that are missing patches, have a vulnerability, or some simple design flaw that exposes them to exploitation. No matter how much security you put into the design of your site, at some point there maybe a change that introduces a security flaw. How do you protect yourself?
As we showed in our previous article, Cloudflare security, fronting access to your site with a service like Cloudflare provides a suite of security tools that you can use to secure your site. Though many of these tools are easy to enable for your site, it is still a great idea to test and validate that the controls are appropriately working. We will show here several tools that you can use to quickly scan your own site for vulnerabilities.
Web application testing
Kali Linux
While this is not a major primer into web application testing, we will be using several tools that are used by professional penetration testers. To start, you will need to get yourself a copy of Kali Linux, a Linux distro specifically made for penetration testing. Head over to kali.org and navigate to their download page. Kali linux provides many types of ways to install their distro. If you are familiar with virtualization software like VirtualBox, KVM, or VMware, they have several ready made virtual images for download that can get you started quickly. You can also choose several other options such as container images, Windows Subsystem for Linux, and of course, ISO images to directly install.
I have used both the VirtualBox image method and the direct installer ISO image. Both are sufficient and provide you with the same installed setup. I personally prefer the ISO image path because I can customize my installation. Once installed and setup, you can find most of the web application testing tools we will use pre-installed and available from the desktop menu.
WhatWeb
Beginning with the most simple tool, WhatWeb is a basic foot-printing application that will scan the site and show you the technologies it can infer based on the responses it receives. You'll be surprised by just how much information it can provide back just based on responses your site provides by navigating to it. On our bakery site, we found the following technologies used:
- Bootstrap
- HTML5
- Hosted on Cloudflare
By determining the technologies used on your site, you can appropriately choose which tools to use to scan for vulnerabilities and weaknesses. Even if the site is your own, there maybe technologies you are not aware of buried in the libraries your frameworks use or in the choices of your hosting providers.
┌──(kali㉿kali)-[~]
└─$ whatweb https://bakery.cakejello.com
https://bakery.cakejello.com [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[cloudflare], IP[172.67.134.139], Script, Title[Bakery Website], UncommonHeaders[cf-cache-status,access-control-allow-origin,referrer-policy,x-content-type-options,report-to,nel,cf-ray]
WhatWeb example
WPScan
A very common choice for websites, especially blogs (not this one though), has historically been Wordpress. A large number of sites on the web use Wordpress to power their blogs. And with its extensive plugin system, its very easy to extend and add features to your site. However, this comes as a double-edged sword as many Wordpress plugins (as well as versions of Wordpress itself) comes with various and sometimes unknown vulnerabilities.
WPScan is a Wordpress specific vulnerability scanner that can be used against a Wordpress site to uncover vulnerabilities and non-secure configurations. It is regularly updated from a central database of known vulnerabilities. Keeping it up-to-date does require an API key but the authors can provide this free and its highly recommended. You can also sign up for a newsletter that will let you know about the latest vulnerabilities published to the database.
I'm not using Wordpress on this site, but you can see what a WPScan looks like and how to initiate it from the command line here.
──(kali㉿kali)-[~]
└─$ wpscan --url https://bakery.cakejello.com --force --api-token $(cat wpscan.api) -o bakery.cakejello.com.wpscan.txt
┌──(kali㉿kali)-[~]
└─$ cat bakery.cakejello.com.wpscan.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.27
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://bakery.cakejello.com/ [172.67.134.139]
[+] Started: Sun May 18 18:45:06 2025
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - cf-cache-status: DYNAMIC
| - server: cloudflare
| - access-control-allow-origin: *
| - referrer-policy: strict-origin-when-cross-origin
| - report-to: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v4?s=dyF45w%2FCDVe3FCKfHeY%2BjGcqaI2tQWc8gvZGQ%2FYVlWmETv0HalNCOJspABkYunqCh4sppg%2B8uQBY8G5AcOoyeRHdi2nWckDvBQDSpR4oYer8IxZ8tGHcZR2hiiIBGsjqMk%2BXErK6qA%3D%3D"}],"group":"cf-nel","max_age":604800}
| - nel: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
| - cf-ray: 941ee200dde3b032-ATL
| Found By: Headers (Passive Detection)
| Confidence: 100%
[i] The WordPress version could not be detected.
[i] The main theme could not be detected.
[i] No plugins Found.
[i] No Config Backups Found.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 0
| Requests Remaining: 25
[+] Finished: Sun May 18 18:46:13 2025
[+] Requests Done: 1629
[+] Cached Requests: 6
[+] Data Sent: 378.808 KB
[+] Data Received: 2.489 MB
[+] Memory used: 238.34 MB
[+] Elapsed time: 00:01:06
WPScan example
Nikto
Nikto is a general purpose web vulnerability scanner that will scan your site for common misconfigurations, weak setups, and vulnerabilities. It is regularly updated and can scan for "over 7000 potentially dangerous files/programs", https://www.cirt.net/Nikto2. It has been around for over 2 decades and is a tried and true web application vulnerability scanner.
Nikto does require a little work playing around with it to get it to scan exactly how you'd like. As a comprehensive scanning tool, it can generate quite a lot of traffic to your site so be aware of that.
┌──(kali㉿kali)-[~]
└─$ nikto -host https://bakery.cakejello.com
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Multiple IPs found: 172.67.134.139, 104.21.6.60, 2606:4700:3030::6815:63c, 2606:4700:3031::ac43:868b
+ Target IP: 172.67.134.139
+ Target Hostname: bakery.cakejello.com
+ Target Port: 443
---------------------------------------------------------------------------
+ SSL Info: Subject: /CN=bakery.cakejello.com
Ciphers: TLS_AES_256_GCM_SHA384
Issuer: /C=US/O=Google Trust Services/CN=WE1
+ Start Time: 2025-05-18 18:47:54 (GMT-4)
---------------------------------------------------------------------------
+ Server: cloudflare
+ /: Retrieved access-control-allow-origin header: *.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The site uses TLS and the Strict-Transport-Security HTTP header is not defined. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Strict-Transport-Security
+ /ZorEv2u7.bat: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: The Content-Encoding header is set to "deflate" which may mean that the server is vulnerable to the BREACH attack. See: http://breachattack.com/
+ ERROR: Error limit (20) reached for host, giving up. Last error: opening stream: can't connect: SSL negotiation failed: error:0A000410:SSL routines::ssl/tls alert handshake failure at /var/lib/nikto/plugins/LW2.pm line 5254.
at /var/lib/nikto/plugins/LW2.pm line 5254.
; at /var/lib/nikto/plugins/LW2.pm line 5254.
+ Scan terminated: 20 error(s) and 5 item(s) reported on remote host
+ End Time: 2025-05-18 18:49:20 (GMT-4) (86 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Nikto example
Wapiti
Like Nikto, Wapiti is a web application vulnerability scanner with many modules and features. It can scan your site for various types of vulnerabilities like Cross-Site Scripting, Database injections, File disclosure vulnerabilities, Command execution, and more. Wapiti can run as a black-box scanner (scanning the site with no knowledge of its internal workings) or as a grey-box scanner (scanning a site with some limited information like a username or password). Wapiti can be run from the command line or from a web browser.
┌──(kali㉿kali)-[~]
└─$ wapiti -u https://bakery.cakejello.com
██╗ ██╗ █████╗ ██████╗ ██╗████████╗██╗██████╗
██║ ██║██╔══██╗██╔══██╗██║╚══██╔══╝██║╚════██╗
██║ █╗ ██║███████║██████╔╝██║ ██║ ██║ █████╔╝
██║███╗██║██╔══██║██╔═══╝ ██║ ██║ ██║ ╚═══██╗
╚███╔███╔╝██║ ██║██║ ██║ ██║ ██║██████╔╝
╚══╝╚══╝ ╚═╝ ╚═╝╚═╝ ╚═╝ ╚═╝ ╚═╝╚═════╝
Wapiti-3.0.4 (wapiti.sourceforge.io)
[*] Saving scan state, please wait...
Note
========
This scan has been saved in the file /home/kali/.wapiti/scans/bakery.cakejello.com_folder_4c628f8c.db
[*] Wapiti found 2 URLs and forms during the scan
[*] Loading modules:
backup, blindsql, brute_login_form, buster, cookieflags, crlf, csp, csrf, exec, file, htaccess, http_headers, methods, nikto, permanentxss, redirect, shellshock, sql, ssrf, wapp, xss, xxe
[*] Launching module csp
CSP is not set
[*] Launching module http_headers
Checking X-Frame-Options :
X-Frame-Options is not set
Checking X-XSS-Protection :
X-XSS-Protection is not set
Checking X-Content-Type-Options :
OK
Checking Strict-Transport-Security :
Strict-Transport-Security is not set
[*] Launching module cookieflags
[*] Launching module exec
[*] Launching module file
[*] Launching module sql
[*] Launching module xss
[*] Launching module ssrf
[*] Asking endpoint URL https://wapiti3.ovh/get_ssrf.php?id=bcpu1s for results, please wait...
[*] Launching module redirect
[*] Launching module blindsql
[*] Launching module permanentxss
Report
------
A report has been generated in the file /home/kali/.wapiti/generated_report
Open /home/kali/.wapiti/generated_report/bakery.cakejello.com_05182025_2305.html with a browser to see this report.
Wapiti example
Cloudflare Security Analytics
As you have run tests against your site for vulnerabilities you can verify how many attacks your Cloudflare instance has mitigated. On your domain's Cloudflare pages, navigate to Security > Analytics. They provide several charts and dashboards to provide you with key metrics about the security responses for your site.
The Security Analytics page has a dashboard right at the top identifying key "suspicious activities" that have occurred against your site. Below that you'll find a chart about traffic that has been mitigated against your site. You can filter this chart by various criteria such as Country, Source browser, Source IP, Operating System, and several others. The chart will show you counts over time to help you visualize mitigations and attack patterns against your site.
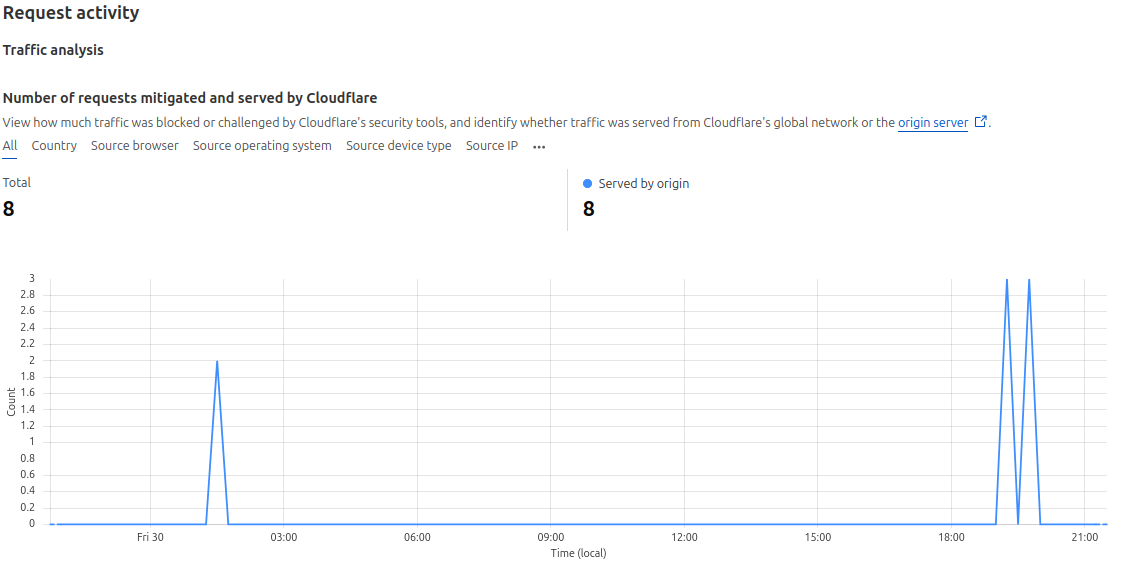
Request activity graph
Additionally there are dashboard panels showing other "Top statistics" using the same criteria as before such as Top source IPs, Top device types, and Top Countries. And finally below that you find a sample of the logs generating those events.
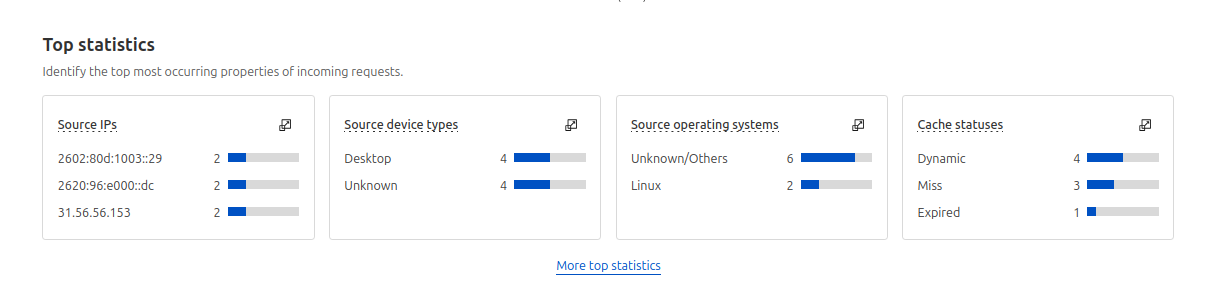
Statistics dashboards
Security Events
Over on the Event tab, you can find a list of sampled logs showing details on blocked actions, mitigations, and other actions. Here you can add filters to dive deeper into the traffic data. Filters include typical criteria such as Source IPs, Country, ASN, Host, but also some more esoteric criteria like HTTP method, Path, Ray ID, Content scan results and others.
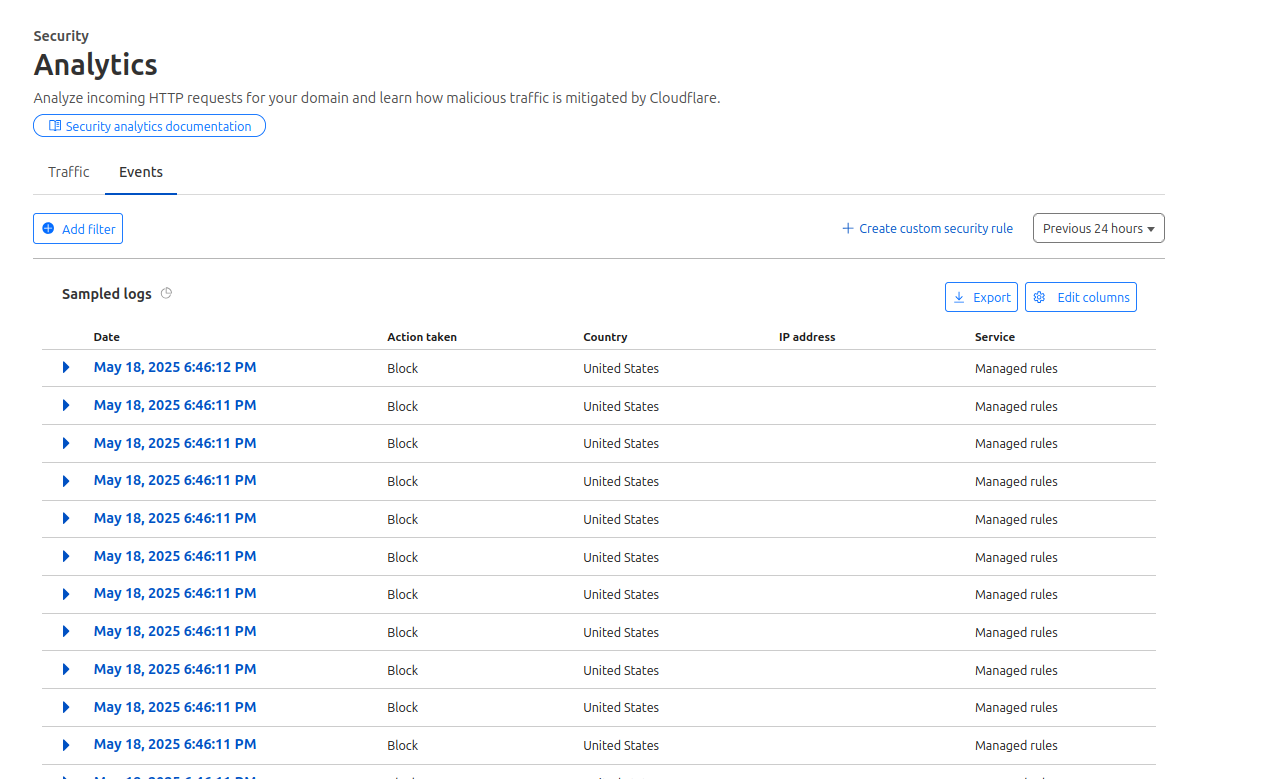
Events list
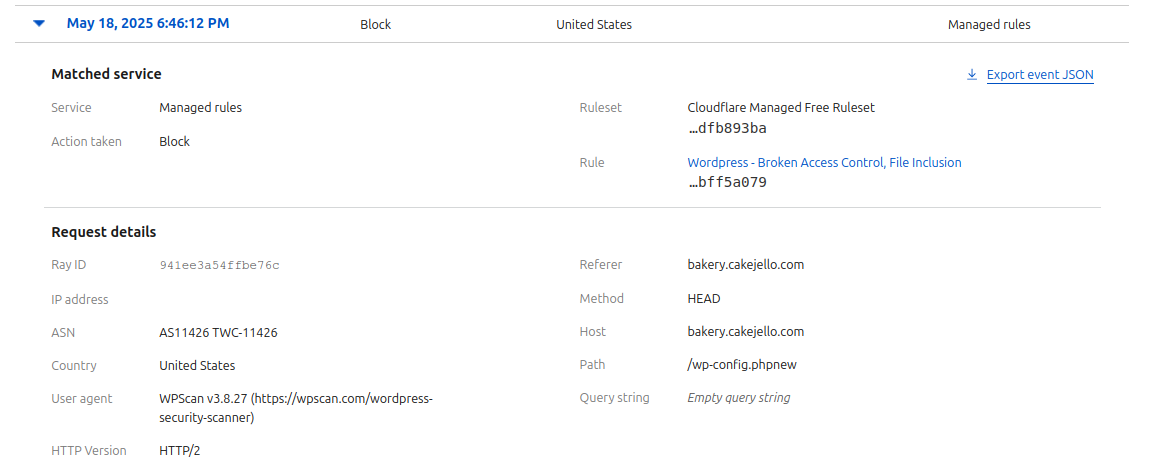
Event details
Limitations
Now of course with all things Cloudflare the options you receive are based on the plan you've purchased. Obviously if you are operating the free plan you will be limited on how analytics are presented as well. For instance, on a free plan your traffic history will be limited to maybe at best a couple of days. The logs available for review are only samples of the traffic mitigations. And you are only able to download audit logs via CSV. In order to integrate with another logging tool like a SIEM (Security Information and Event Management) system you'll need an Enterprise license.
Summary
In this article we went over several tools you can use to test your website and how to verify that the security you've setup on Cloudflare is protecting that website. This, obviously, has not been an exhaustive review or tutorial on any of these tools. I recommend if you are interested in performing your own web application security tests that you spend time reading the documentation of each of the tools you are using to best apply their capabilities to your security scan.
Cheers!
References
Kali Linux - https://www.kali.org/
WhatWeb - https://whatweb.net/
WPScan - https://wpscan.com/
WPScan registration (gets you an API key) - https://wpscan.com/register/
Nikto - https://www.cirt.net/Nikto2
Wapiti - https://www.kali.org/tools/wapiti/
Cloudflare - https://www.cloudflare.com/



